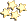My findings:
Truecrypt 5.0a is a free open source data encryption solution for Windows, OSX and Linux.
It's capable of encrypting a container file, partition, or even your OS partition and entire drive. The site mentions several reasons why it's a better solution than Bitlocker which I won't get in to.
I've mention the free app called Erasor before which can permanently delete data from your hard drive overwriting the data several times with various random patterns and 0's and 1's depending on how paranoid you are. I've been using that to delete my temp newleecher directory files after sometimes opening questionable files directly from newsleecher. It's a great little app and works well but instead of stressing over random files here and there, I used Truecrypt and created a 100GB file container and located all of my newsleecher downloads, config files, group history storage, temp files, etc inside the container.
A Truecrypt container (as opposed to encrypting an entire partition) can be mounted as a hard drive easily and can be left open as long as the computer is running. It automatically dismounts if the PC is turned off or there's a power outage. The mounted container file is visible to all apps just like any other partition.
I was a little worried about how much encryption would slow things down. Truecrypt has heavy duty encryption options:


After reading up on AES, Twofish and Serpent, it appears they're all excellent 256-bit encryption. If you are off-the-charts paranoid, you can also combine two or all three of them. I wanted the fastest one but accidentally chose Serpent instead of Twofish. It took about 60 minutes to setup a 100GB encryption container. As you can see above (if not red-x'd!), Twofish would have taken about half that time.
Newleecher makes it easy to change locations for the temp file, storage folder, etc so that didn't take long. Basically, I just need to remember to mount the container before using Newsleecher. If I forget, Newsleecher warns you that it can't access the storage locations anyway when it opens so that's a good reminder.
I haven't been able to fully test the speed but so for the few files I downloaded, it seemed ok. It wasn't enough to see if I was getting full transfer speeds etc so will try that out tonight. If anything appears slow, I'll switch to the Twofish encryption option that I originally meant to use.
----
Anyways, Truecrypt has a nice "travel" encryption solution which made me think of the article posted here recently where someone with a notebook traveling across the US/Canada border had an encrypted partition and the authorities were trying to force him to give his password.
Truecrypt has a way for "Plausible Deniability' if this happens to you. In short, you create a hidden encrypted container within a visible encrypted container or partition. Encrypted partitions or containers are always filled with random data when they are created so to someone that doesn't have the key, there's no way to tell that there's a hidden volume within the visible volume. When you attempt to access the visible volume, Truecrypt asks you for your password. Truecrypt will open either the visible or hidden container depending on which password you enter. (of course you create two different passwords).
With this strategy, you would put something like pr0n or a picture of Stragi in the visible container which would appear embarrassing if you were caught with it but not too bad, and then you'd store the actual sensitive data in the hidden container. If forced to give up your password, you'd give the visible container password and there'd be no way to tell that a hidden container exists.
The second "Plausible Deniability" suggestion is to not use the .tc extension for your container. Truecrypt completely ignores the filename and extension for container files. so you could name your file whatever you want and give it any extension you want or no extension at all. Without the .tc extension, there's no cause to believe you have an encrypted container.
-----
Cool stuff. I really don't have anything that interesting to hide but I also don't want to bother with having to erase my temp folder, etc. and figure it couldn't hurt to download everything into an encrypted folder and then move stuff that I want to keep out of it. 100GB is large enough to not have to micromanage it though.
The Truecrypt website has great documentation and also very active forums. It's worth looking into if just to make a little folder for your tax info, identification info and other crap like personal photos, etc.
http://www.truecrypt.org/docs/